During reconaissance phase or when doing OSINT , we often use google dorking and shodan and thus the idea of …
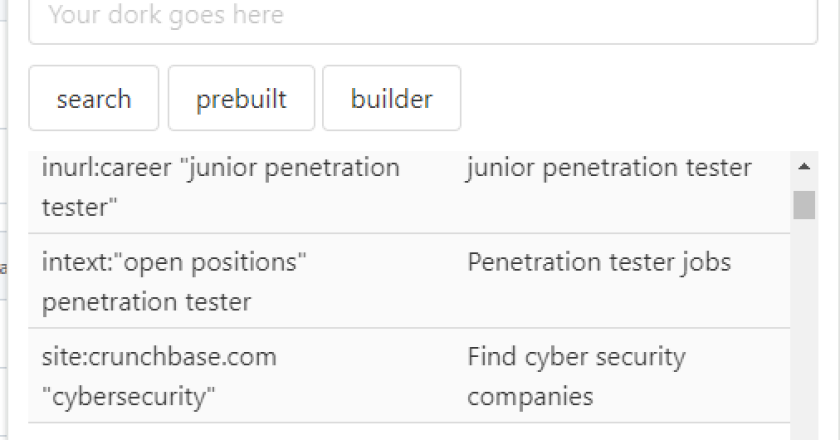

During reconaissance phase or when doing OSINT , we often use google dorking and shodan and thus the idea of …
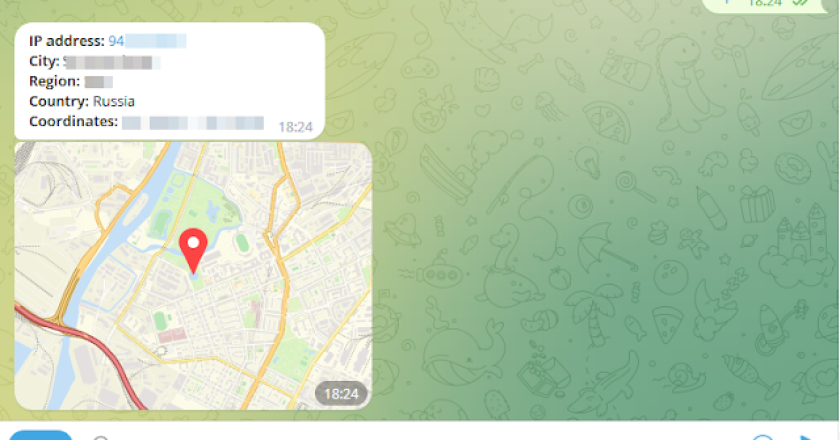
Remote administration crossplatfrom tool via telegram\ Coded with ❤️ python3 + aiogram3\ https://t.me/pt_soft v0.3 [X] Screenshot from target [X] Crossplatform …
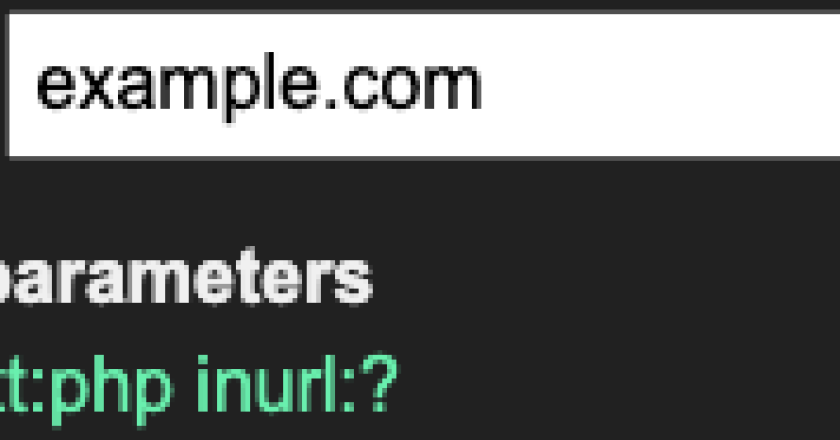
A list of Google Dorks for Bug Bounty, Web Application Security, and Pentesting Live Tool Broad domain search w/ negative …

GTFOcli it’s a Command Line Interface for easy binaries search commands that can be used to bypass local security restrictions …

nomore403 is an innovative tool designed to help cybersecurity professionals and enthusiasts bypass HTTP 40X errors encountered during web security …

This script changes the MAC address of the network interface to a randomly generated address on system startup using crontab. …
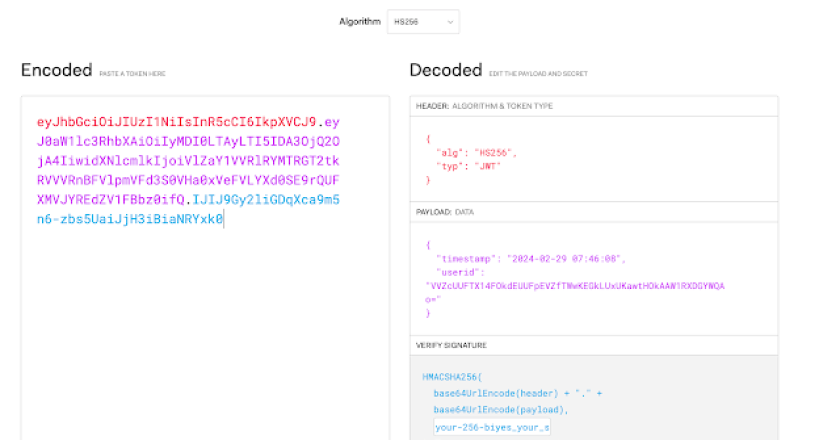
some-tweak-to-hide-jwt-payload-values a handful of tweaks and ideas to safeguard the JWT payload, making it futile to attempt decoding by constantly …

SSH Private Key Looting Wordlists. A Collection Of Wordlists To Aid In Locating Or Brute-Forcing SSH Private Key File Names. …

Mobile Helper Framework is a tool that automates the process of identifying the framework/technology used to create a mobile application. …
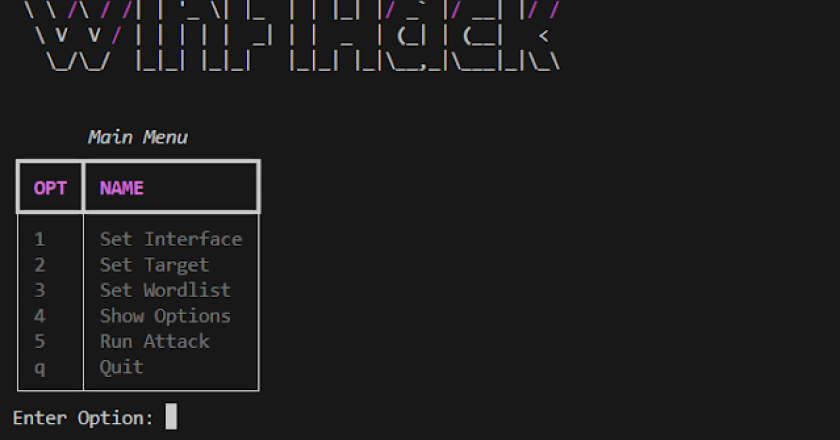
WinFiHack is a recreational attempt by me to rewrite my previous project Brute-Hacking-Framework’s main wifi hacking script that uses netsh …