Frogy 2.0 is an automated external reconnaissance and Attack Surface Management (ASM) toolkit designed to map out an organization’s entire …
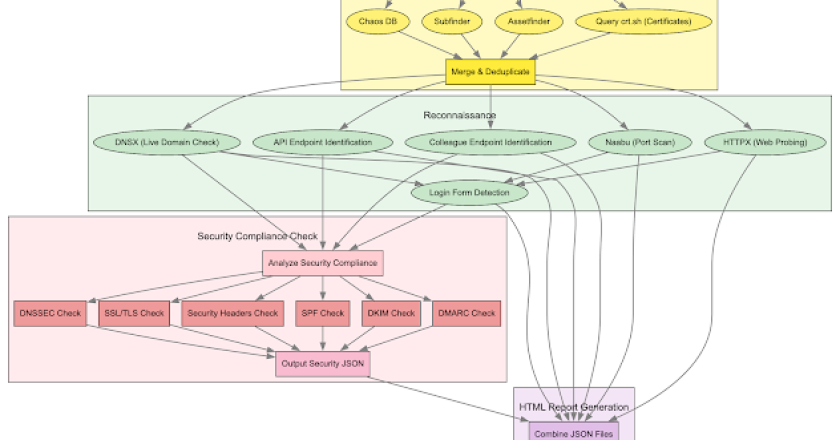

Frogy 2.0 is an automated external reconnaissance and Attack Surface Management (ASM) toolkit designed to map out an organization’s entire …

TL;DR: Galah (/ɡəˈlɑː/ – pronounced ‘guh-laa’) is an LLM (Large Language Model) powered web honeypot, currently compatible with the OpenAI …
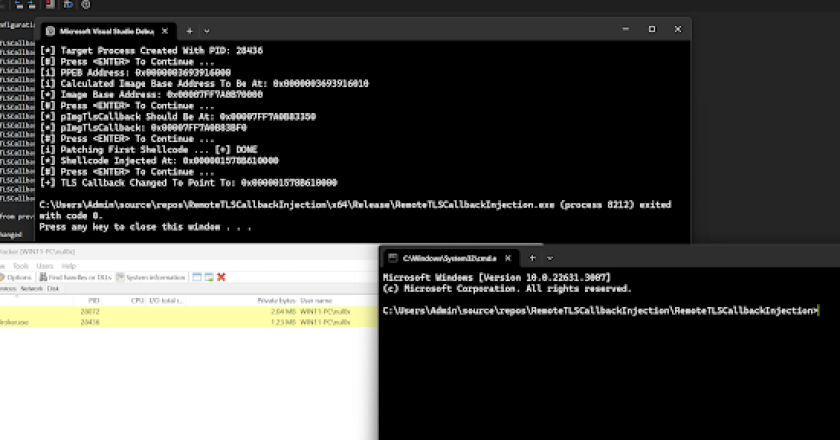
This method utilizes TLS callbacks to execute a payload without spawning any threads in a remote process. This method is inspired by Threadless …

This tool takes a scanning tool’s output file, and converts it to a tabular format (CSV, XLSX, or text table). …

Finding assets from certificates! Scan the web! Tool presented @DEFCON 31 ** You must have CGO enabled, and may have …
File Upload Restrictions Bypass, By Using Different Bug Bounty Techniques! POC video: File upload restrictions bypass by using different bug …
laZzzy is a shellcode loader that demonstrates different execution techniques commonly employed by malware. laZzzy was developed using different open-source …
peetch is a collection of tools aimed at experimenting with different aspects of eBPF to bypass TLS protocol protections. Currently, …
Passive-Recursive DNS daemon. Quickstart <div class="highlight highlight-source-shell notranslate position-relative overflow-auto" data-snippet-clipboard-copy-content="go get github.com/korc/PR-DNSd sudo setcap cap_net_bind_service,cap_sys_chroot=ep go/bin/PR-DNSd go/bin/PR-DNSd -upstream 9.9.9.9:53 …
Please read the initial JARM blog post for more information. JARM is an active Transport Layer Security (TLS) server fingerprinting …