secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it …


secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it …
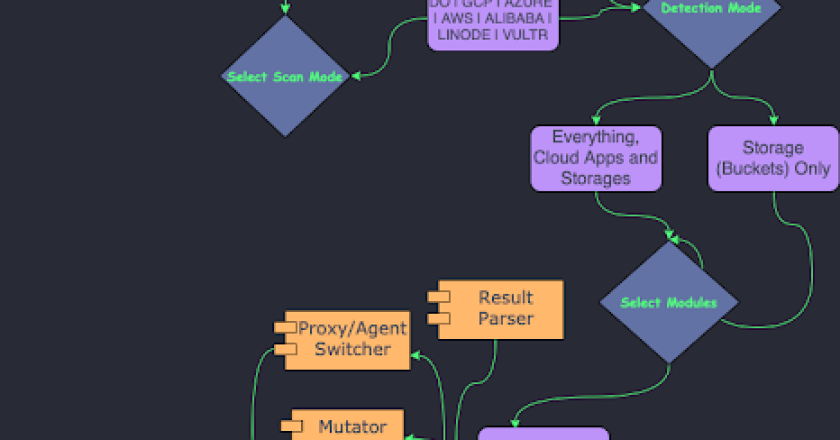
A tool to find a company (target) infrastructure, files, and apps on the top cloud providers (Amazon, Google, Microsoft, DigitalOcean, …

First, a couple of useful oneliners 😉 wget “https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh” -O lse.sh;chmod 700 lse.sh curl “https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh” -Lo lse.sh;chmod 700 lse.sh Note …
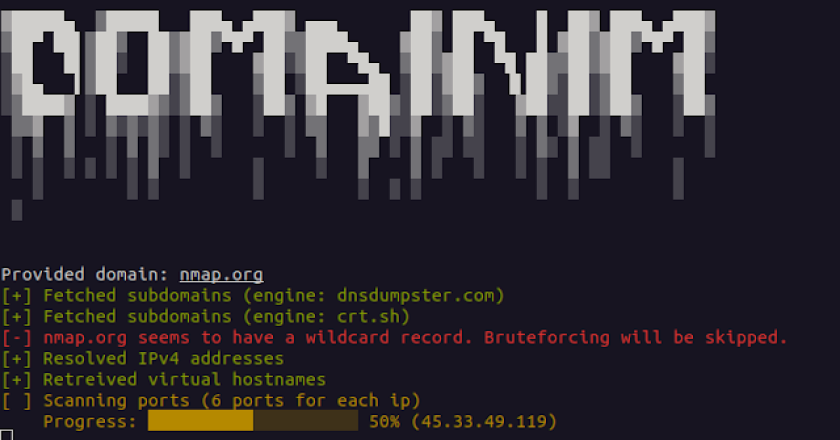
Domainim is a fast domain reconnaissance tool for organizational network scanning. The tool aims to provide a brief overview of …

Subdomain takeover is a common vulnerability that allows an attacker to gain control over a subdomain of a target domain …
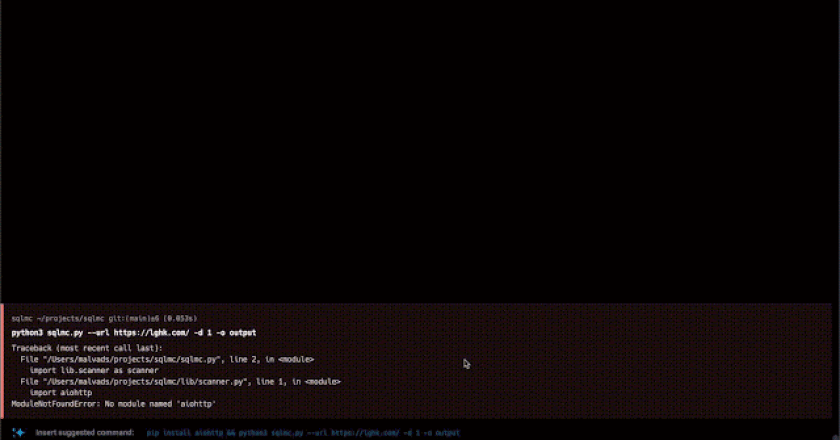
SQLMC (SQL Injection Massive Checker) is a tool designed to scan a domain for SQL injection vulnerabilities. It crawls the …
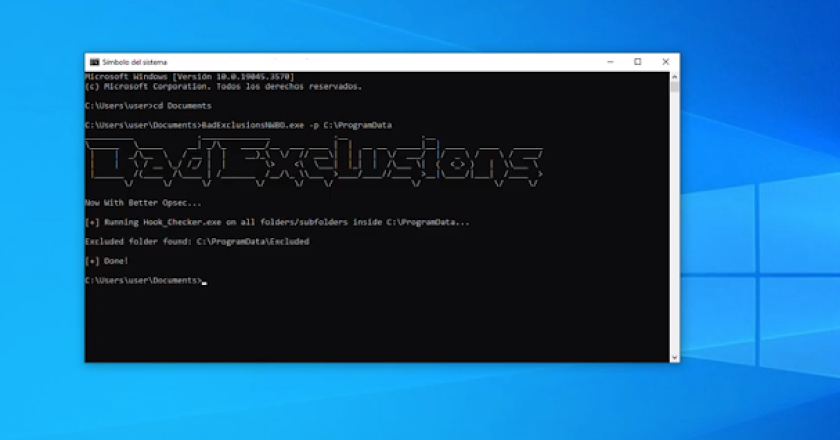
BadExclusionsNWBO is an evolution from BadExclusions to identify folder custom or undocumented exclusions on AV/EDR. BadExclusionsNWBO copies and runs Hook_Checker.exe …
Pentest Muse is an AI assistant tailored for cybersecurity professionals. It can help penetration testers brainstorm ideas, write payloads, analyze …

Essential utilities for pentester, bug-bounty hunters and security researchers secbutler is a utility tool made for pentesters, bug-bounty hunters and …

Rayder is a command-line tool designed to simplify the orchestration and execution of workflows. It allows you to define a …