A utility for identifying web page inputs and conducting XSS scanning. Features: Subdomain Discovery: Retrieves relevant subdomains for the target …


A utility for identifying web page inputs and conducting XSS scanning. Features: Subdomain Discovery: Retrieves relevant subdomains for the target …
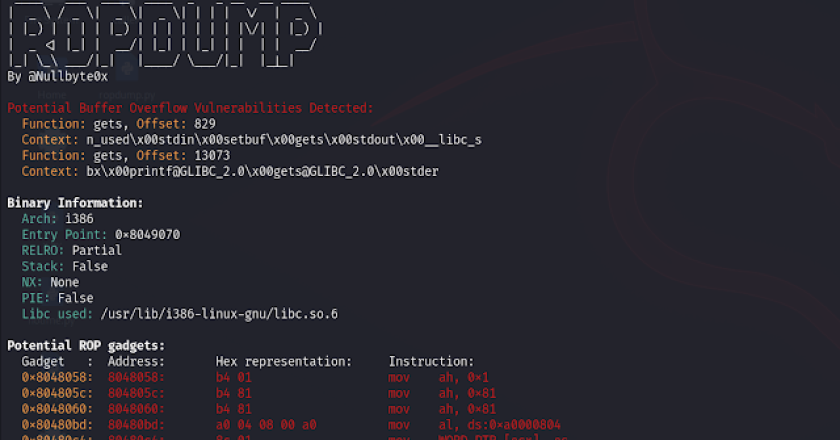
ROPDump is a tool for analyzing binary executables to identify potential Return-Oriented Programming (ROP) gadgets, as well as detecting potential …
This is a simple SBOM utility which aims to provide an insider view on which packages are getting executed. The …

A Slack Attack Framework for conducting Red Team and phishing exercises within Slack workspaces. Disclaimer This tool is intended for …

Reaper is a proof-of-concept designed to exploit BYOVD (Bring Your Own Vulnerable Driver) driver vulnerability. This malicious technique involves inserting …

Howdy! My name is Harrison Richardson, or rs0n (arson) when I want to feel cooler than I really am. The …
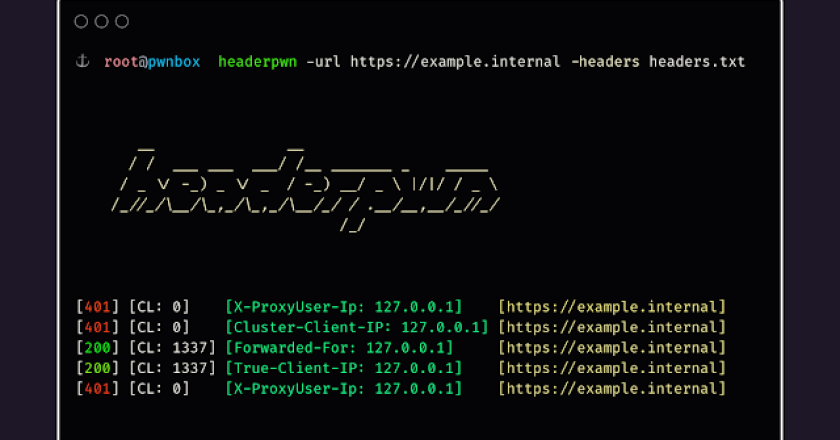
To install headerpwn, run the following command: go install github.com/devanshbatham/[email protected] headerpwn allows you to test various headers on a target …
A tool to generate a wordlist from the information present in LDAP, in order to crack non-random passwords of domain …

First, a couple of useful oneliners 😉 wget “https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh” -O lse.sh;chmod 700 lse.sh curl “https://github.com/diego-treitos/linux-smart-enumeration/releases/latest/download/lse.sh” -Lo lse.sh;chmod 700 lse.sh Note …

SherlockChain is a powerful smart contract analysis framework that combines the capabilities of the renowned Slither tool with advanced AI-powered …