This tool is designed to interact with the GitHub API and retrieve specific user details, repository information, and commit emails …


This tool is designed to interact with the GitHub API and retrieve specific user details, repository information, and commit emails …

OSINT Tool for research social media accounts by username Install Requests “`Install Requests pip install requests #### Install BeautifulSoup“`Install BeautifulSouppip …

Secure, Automated, and Multi-Cloud Bitwarden Backup and Import System Lazywarden is a Python automation tool designed to Backup and Restore …
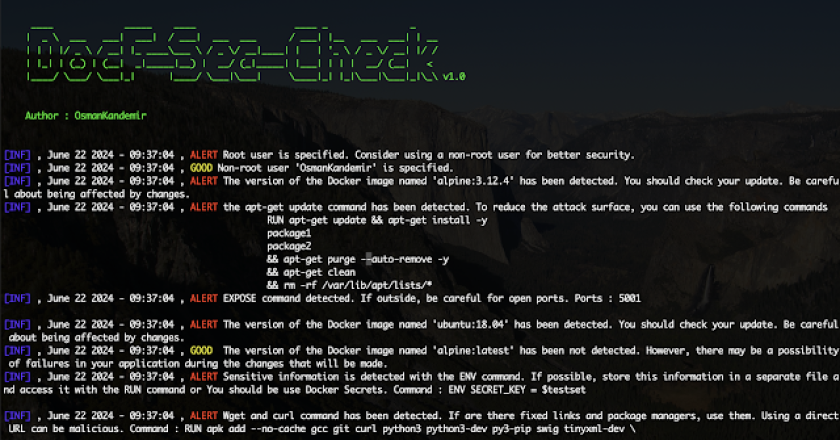
DockF-Sec-Check helps to make your Dockerfile commands more secure. Done [x] First-level security notification in the Dockerfile TODO List [ …

SafeLine is a self-hosted WAF(Web Application Firewall) to protect your web apps from attacks and exploits. A web application firewall …

– Bring-Your-Own-Script-Interpreter – Leveraging the abuse of trusted applications, one is able to deliver a compatible script interpreter for a …

secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it …

file-unpumper is a powerful command-line utility designed to clean and analyze Portable Executable (PE) files. It provides a range of …

Mass Assigner is a powerful tool designed to identify and exploit mass assignment vulnerabilities in web applications. It achieves this …

A make an LKM rootkit visible again. It involves getting the memory address of a rootkit’s “show_module” function, for example, …