A collection of fully-undetectable process injection techniques abusing Windows Thread Pools. Presented at Black Hat EU 2023 Briefings under the …


A collection of fully-undetectable process injection techniques abusing Windows Thread Pools. Presented at Black Hat EU 2023 Briefings under the …
Package go-secdump is a tool built to remotely extract hashes from the SAM registry hive as well as LSA secrets …

Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security engineers. Above: Invisible network protocol snifferDesigned …

V’ger is an interactive command-line application for post-exploitation of authenticated Jupyter instances with a focus on AI/ML security operations. User …
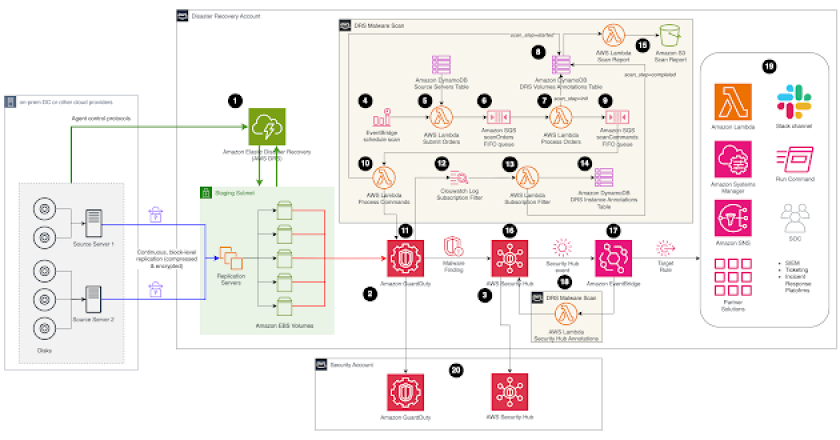
Challenges with on-premises malware detection It can be difficult for security teams to continuously monitor all on-premises servers due to …

An open-source, prototype implementation of property graphs for JavaScript based on the esprima parser, and the EsTree SpiderMonkey Spec. JAW …

Hakuin is a Blind SQL Injection (BSQLI) optimization and automation framework written in Python 3. It abstracts away the inference …

Tags: Aspx, Encryption, Entropy, Hashes, Malware, Obfuscation, PowerShell, Processes, Scan, Scanning, Scripts, Toolbox, ShellSweep ShellSweep – ShellSweeping the evil. Shellsweep …

Retrieve and display information about active user sessions on remote computers. No admin privileges required. The tool leverages the remote …

Subdomain takeover is a common vulnerability that allows an attacker to gain control over a subdomain of a target domain …