Evade EDR’s the simple way, by not touching any of the API’s they hook. Theory I’ve noticed that most EDRs …


Evade EDR’s the simple way, by not touching any of the API’s they hook. Theory I’ve noticed that most EDRs …
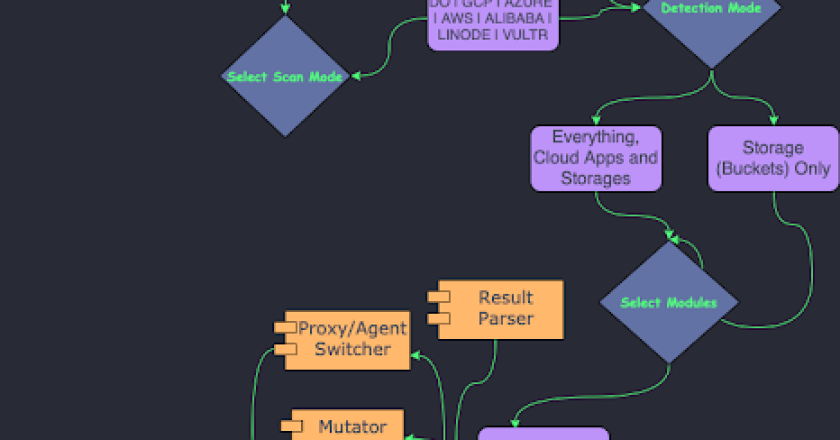
A tool to find a company (target) infrastructure, files, and apps on the top cloud providers (Amazon, Google, Microsoft, DigitalOcean, …

A proof-of-concept User-Defined Reflective Loader (UDRL) which aims to recreate, integrate, and enhance Cobalt Strike’s evasion features! Contributors: UDRL Usage …

Shell command obfuscation to avoid SIEM/detection system During pentest, an important aspect is to be stealth. For this reason you …
BadExclusionsNWBO is an evolution from BadExclusions to identify folder custom or undocumented exclusions on AV/EDR. BadExclusionsNWBO copies and runs Hook_Checker.exe …

The C2 Cloud is a robust web-based C2 framework, designed to simplify the life of penetration testers. It allows easy …
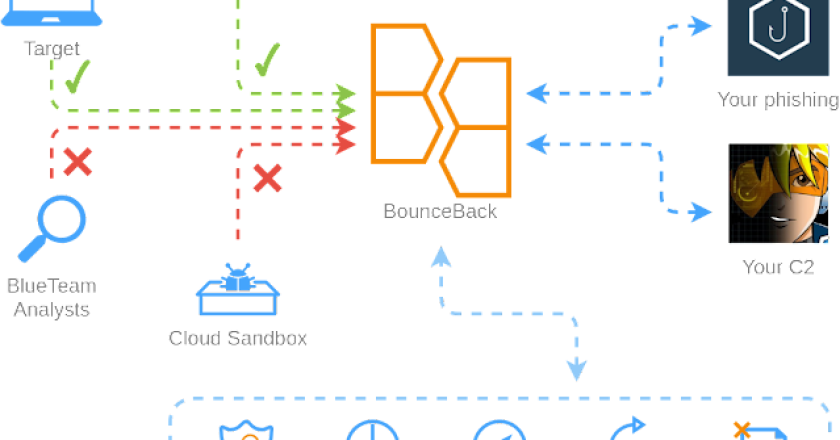
BounceBack is a powerful, highly customizable and configurable reverse proxy with WAF functionality for hiding your C2/phishing/etc infrastructure from blue …

This is a tool designed for Open Source Intelligence (OSINT) purposes, which helps to gather information about employees of a …
A GUI tool for viewing Windows Named Pipes and searching for insecure permissions. The tool was published as part of …
Hades is a basic Command & Control server built using Python. It is currently extremely bare bones, but I plan …