Rayder is a command-line tool designed to simplify the orchestration and execution of workflows. It allows you to define a …


Rayder is a command-line tool designed to simplify the orchestration and execution of workflows. It allows you to define a …

Introducing Uscrapper 2.0, A powerfull OSINT webscrapper that allows users to extract various personal information from a website. It leverages …
gssapi-abuse was released as part of my DEF CON 31 talk. A full write up on the abuse vector can …

This is a tool I whipped up together quickly to DCSync utilizing ESC1. It is quite slow but otherwise an …

FalconHound is a blue team multi-tool. It allows you to utilize and enhance the power of BloodHound in a more …
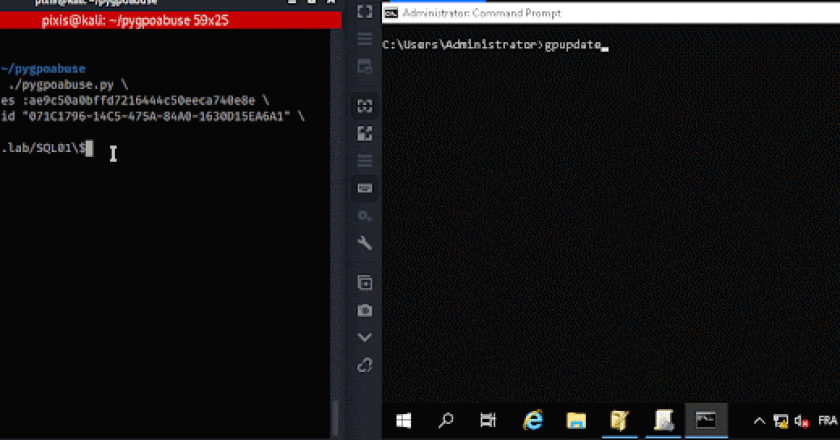
Python partial implementation of SharpGPOAbuse by@pkb1s This tool can be used when a controlled account can modify an existing GPO …

Finding assets from certificates! Scan the web! Tool presented @DEFCON 31 ** You must have CGO enabled, and may have …
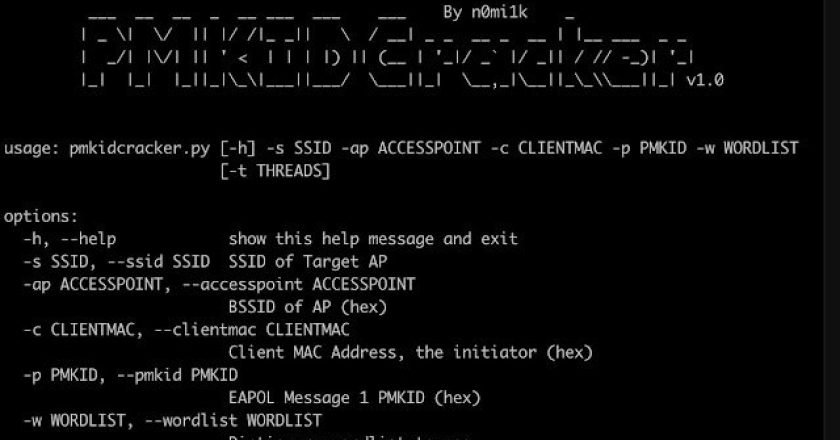
This program is a tool written in Python to recover the pre-shared key of a WPA2 WiFi network without any …

Description Easy EASM is just that… the easiest to set-up tool to give your organization visibility into its external facing …

iCloud can be an easy and secure way to back up photos and videos, but accessing those files across devices …