Tool for analyzing SAP Secure Network Communications (SNC). In its current state, sncscan can be used to read the SNC …
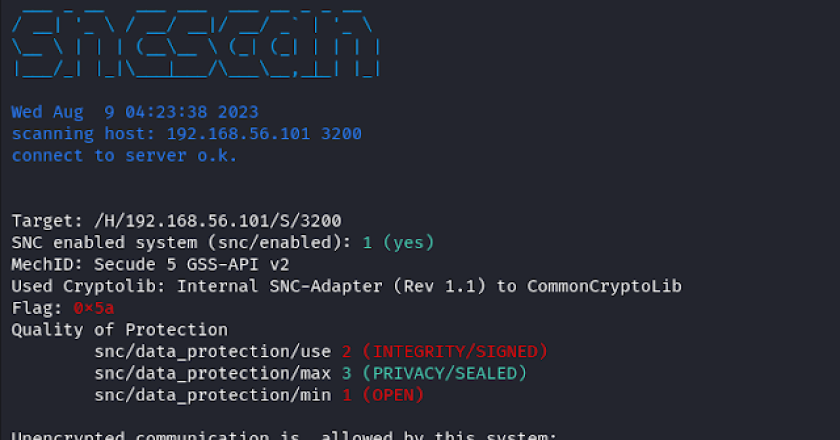

Tool for analyzing SAP Secure Network Communications (SNC). In its current state, sncscan can be used to read the SNC …
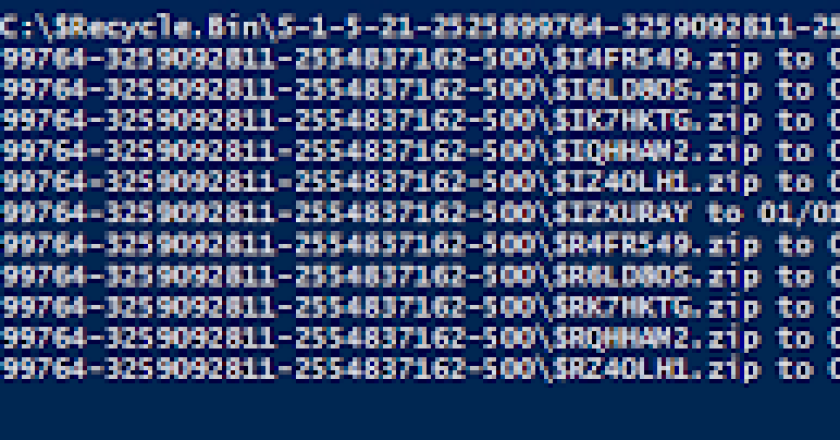
A PowerShell function to perform timestomping on specified files and directories. The function can modify timestamps recursively for all files …
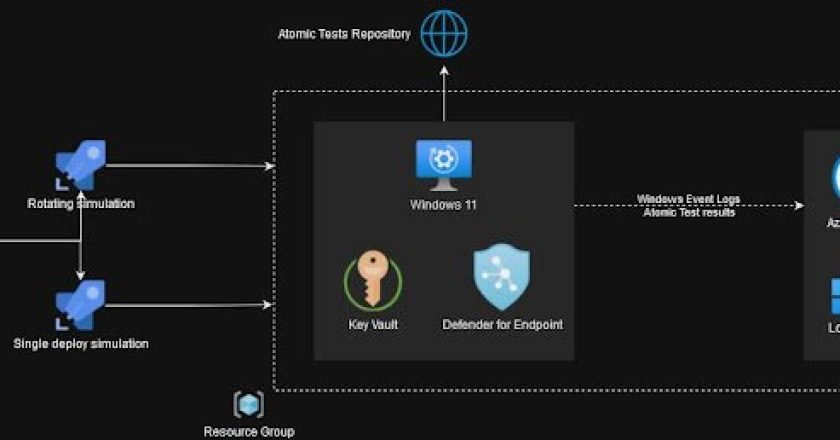
With the rapidly increasing variety of attack techniques and a simultaneous rise in the number of detection rules offered by …
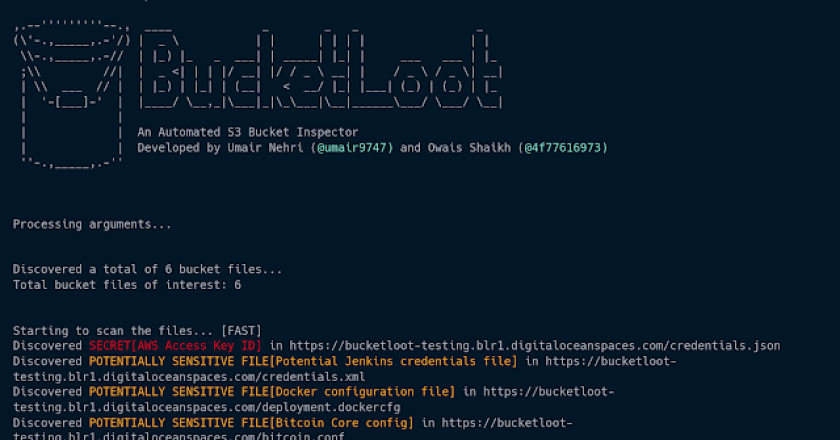
BucketLoot is an automated S3-compatible Bucket inspector that can help users extract assets, flag secret exposures and even search for …

RAVEN (Risk Analysis and Vulnerability Enumeration for CI/CD) is a powerful security tool designed to perform massive scans for GitHub …
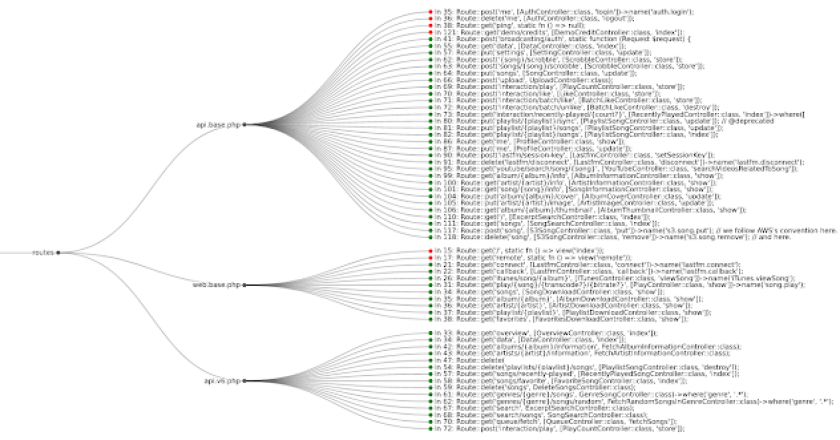
Find authentication (authn) and authorization (authz) security bugs in web application routes: Web application HTTP route authn and authz bugs …
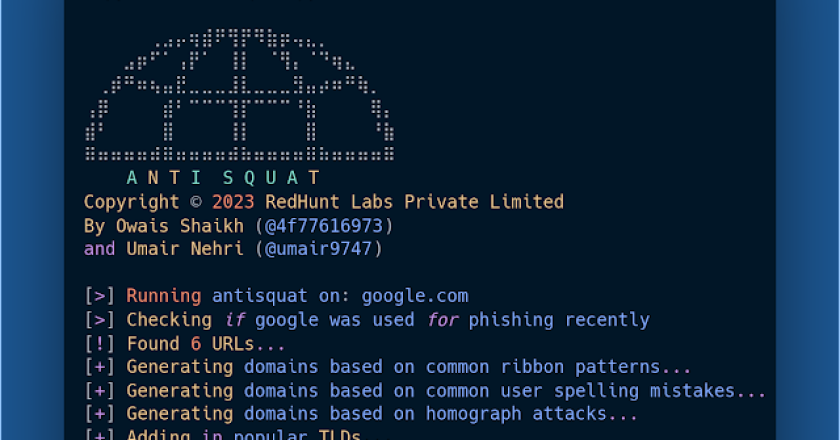
AntiSquat leverages AI techniques such as natural language processing (NLP), large language models (ChatGPT) and more to empower detection of …
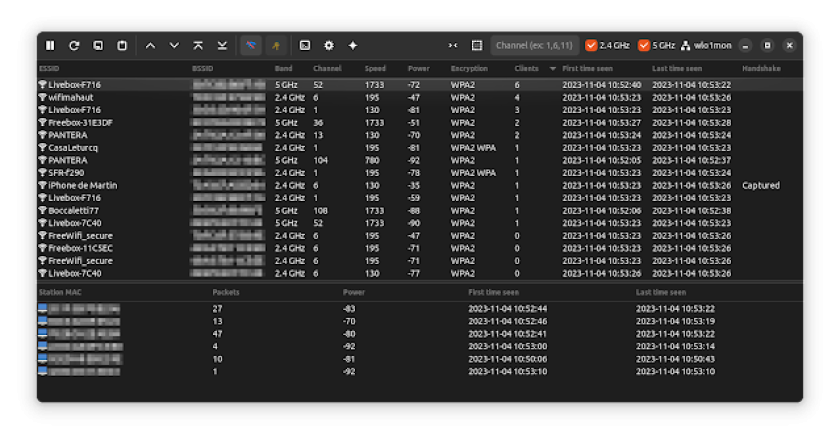
Airgorah is a WiFi auditing software that can discover the clients connected to an access point, perform deauthentication attacks against …

Rayder is a command-line tool designed to simplify the orchestration and execution of workflows. It allows you to define a …

Introducing Uscrapper 2.0, A powerfull OSINT webscrapper that allows users to extract various personal information from a website. It leverages …