A make an LKM rootkit visible again. It involves getting the memory address of a rootkit’s “show_module” function, for example, …


A make an LKM rootkit visible again. It involves getting the memory address of a rootkit’s “show_module” function, for example, …
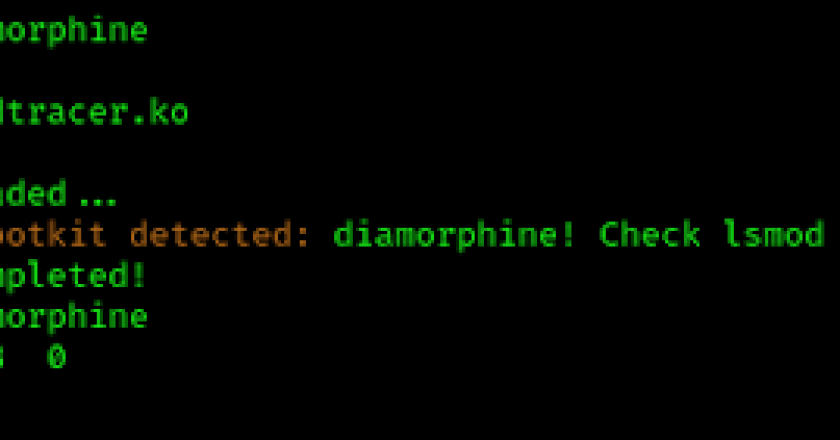
ModTracer Finds Hidden Linux Kernel Rootkits and then make visible again. Another way to make an LKM visible is using the imperius trick: https://github.com/MatheuZSecurity/Imperius …

PoCs for Kernelmode rootkit techniques research or education. Currently focusing on Windows OS. All modules support 64bit OS only. NOTE …

Demonized Shell is an Advanced Tool for persistence in linux. Install git clone https://github.com/MatheuZSecurity/D3m0n1z3dShell.gitcd D3m0n1z3dShellchmod +x demonizedshell.shsudo ./demonizedshell.sh One-Liner Install …
VED (Vault Exploit Defense)-eBPF leverages eBPF (extended Berkeley Packet Filter) to implement runtime kernel security monitoring and exploit detection for …
A Linux persistence tool! A powerful and versatile Linux persistence script designed for various security assessment and testing scenarios. This …
Hidden has been developed like a solution for reverse engineering and researching tasks. This is a windows driver with a …
Ring 3 rootkit r77 is a ring 3 Rootkit that hides following entities from all processes: Files, directories, junctions, named …
Scan your EC2 instance to find its vulnerabilities using Vuls (https://vuls.io/en/). Audit your EC2 instance to find security misconfigurations using …
The WinPmem memory acquisition driver and userspace WinPmem has been the default open source memory acquisition driver for windows for …