This GitHub repository provides a range of search queries, known as “dorks,” for Shodan, a powerful tool used to search …


This GitHub repository provides a range of search queries, known as “dorks,” for Shodan, a powerful tool used to search …
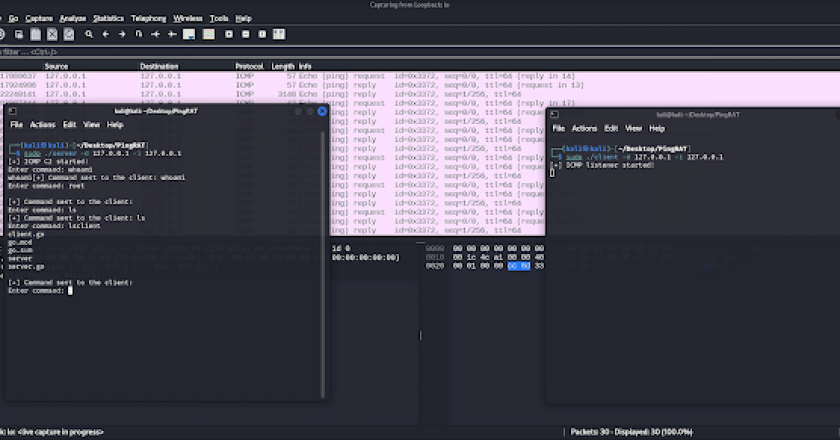
PingRAT secretly passes C2 traffic through firewalls using ICMP payloads. Features: Uses ICMP for Command and Control Undetectable by most …
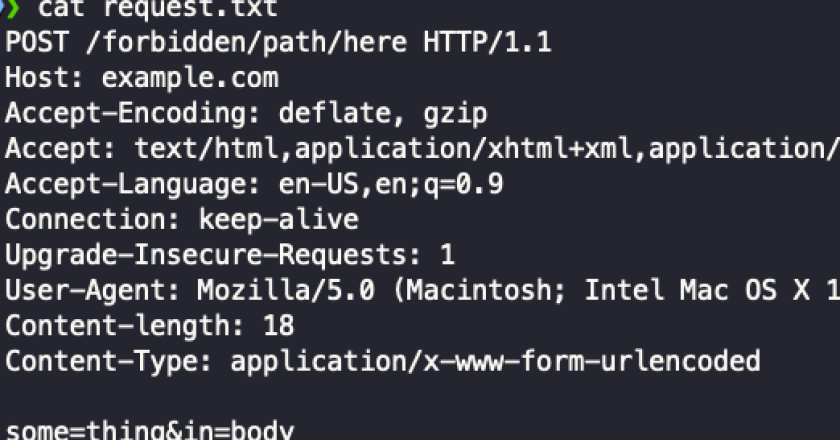
The original 403fuzzer.py 🙂 Fuzz 401/403ing endpoints for bypasses This tool performs various checks via headers, path normalization, verbs, etc. …
Mass bruteforce network protocols Info Simple personal script to quickly mass bruteforce common services in a large scale of network.It …
Commander is a command and control framework (C2) written in Python, Flask and SQLite. It comes with two agents written in …
HBSQLI is an automated command-line tool for performing Header Based Blind SQL injection attacks on web applications. It automates the …
Spoofy is a program that checks if a list of domains can be spoofed based on SPF and DMARC records. …
This project was built by pentesters for pentesters. Redeye is a tool intended to help you manage your data during …
msLDAPDump simplifies LDAP enumeration in a domain environment by wrapping the lpap3 library from Python in an easy-to-use interface. Like …
<meta content="Signing-key abuse and update exploitation framework. % docker run -it –rm ghcr.io/kpcyrd/sh4d0wup:edge -h Usage: sh4d0wup [OPTIONS] <meta content="Signing-key abuse …