secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it …


secator is a task and workflow runner used for security assessments. It supports dozens of well-known security tools and it …
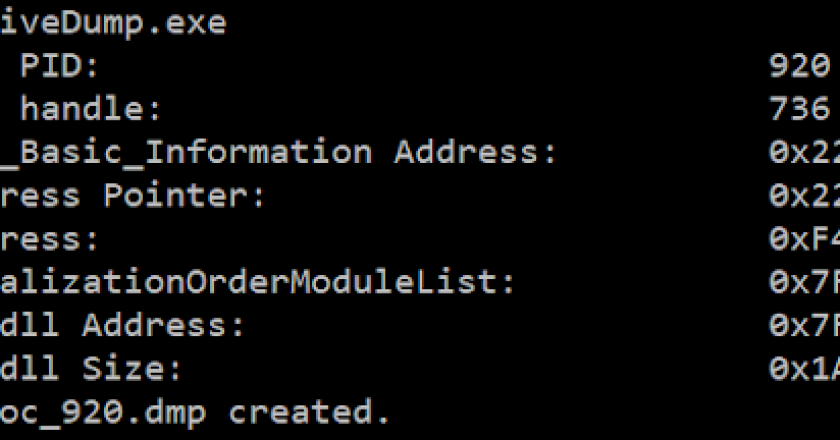
NativeDump allows to dump the lsass process using only NTAPIs generating a Minidump file with only the streams needed to …

Invisible protocol sniffer for finding vulnerabilities in the network. Designed for pentesters and security engineers. Above: Invisible network protocol snifferDesigned …

Subdomain takeover is a common vulnerability that allows an attacker to gain control over a subdomain of a target domain …

TL;DR: Galah (/ɡəˈlɑː/ – pronounced ‘guh-laa’) is an LLM (Large Language Model) powered web honeypot, currently compatible with the OpenAI …
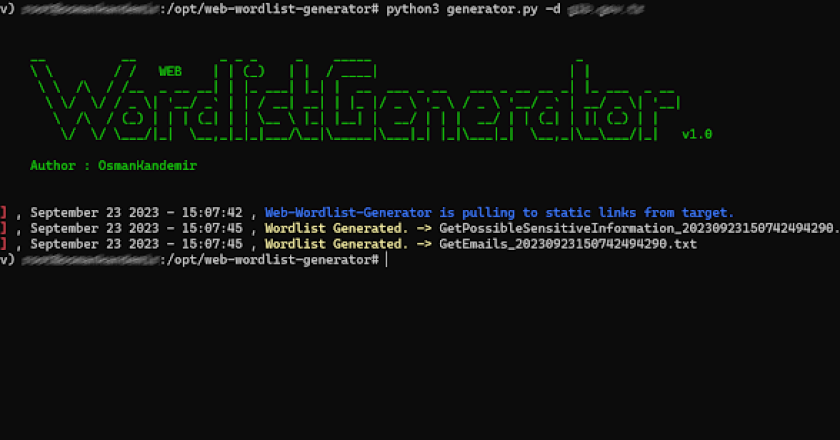
WEB-Wordlist-Generator scans your web applications and creates related wordlists to take preliminary countermeasures against cyber attacks. Done [x] Scan Static …

RAVEN (Risk Analysis and Vulnerability Enumeration for CI/CD) is a powerful security tool designed to perform massive scans for GitHub …

Have you ever watched a film where a hacker would plug-in, seemingly ordinary, USB drive into a victim’s computer and …
Afuzz is an automated web path fuzzing tool for the Bug Bounty projects. Afuzz is being actively developed by @rapiddns …
SecuSphere is a comprehensive DevSecOps platform designed to streamline and enhance your organization’s security posture throughout the software development life …