V’ger is an interactive command-line application for post-exploitation of authenticated Jupyter instances with a focus on AI/ML security operations. User …


V’ger is an interactive command-line application for post-exploitation of authenticated Jupyter instances with a focus on AI/ML security operations. User …

LOLSpoof is a an interactive shell program that automatically spoof the command line arguments of the spawned process. Just call …
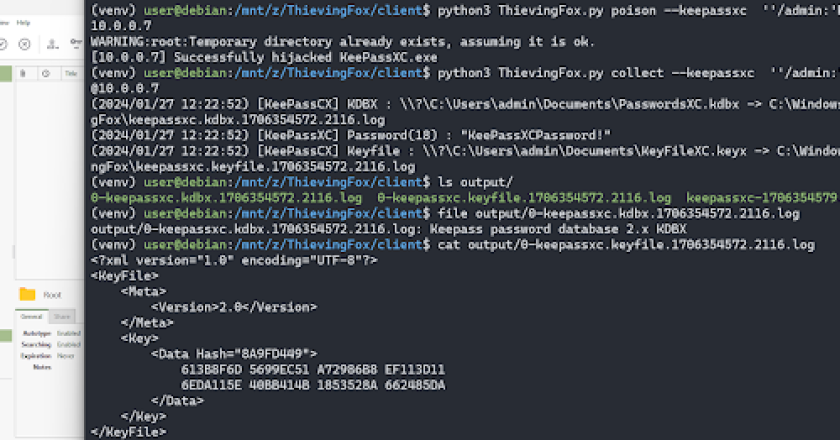
ThievingFox is a collection of post-exploitation tools to gather credentials from various password managers and windows utilities. Each module leverages …
This post-exploitation keylogger will covertly exfiltrate keystrokes to a server. These tools excel at lightweight exfiltration and persistence, properties which …
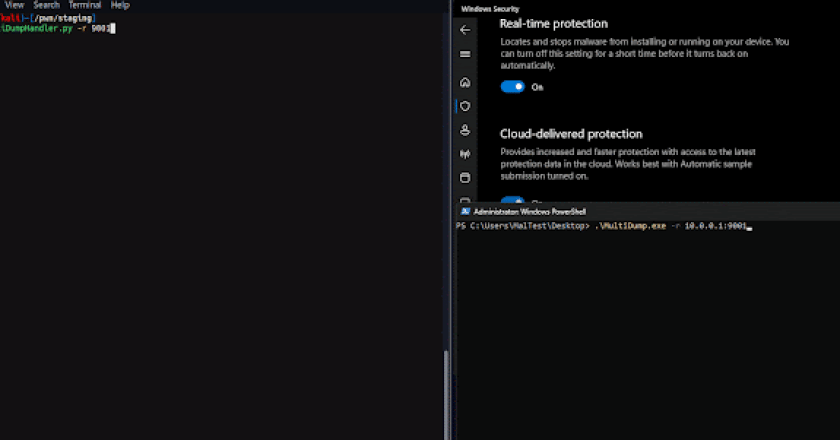
MultiDump is a post-exploitation tool written in C for dumping and extracting LSASS memory discreetly, without triggering Defender alerts, with …

Nemesis is an offensive data enrichment pipeline and operator support system. Built on Kubernetes with scale in mind, our goal …
A stealth post-exploitation container. Introduction With the raise in popularity of offensive tools based on eBPF, going from credential stealers …
Rapidly host payloads and post-exploitation bins over HTTP or HTTPS. Designed to be used on exams like OSCP / PNPT …
WindowSpy is a Cobalt Strike Beacon Object File meant for targetted user surveillance. The goal of this project was to …
Havoc is in an early state of release. Breaking changes may be made to APIs/core structures as the framework matures. …