NoArgs is a tool designed to dynamically spoof and conceal process arguments while staying undetected. It achieves this by hooking …
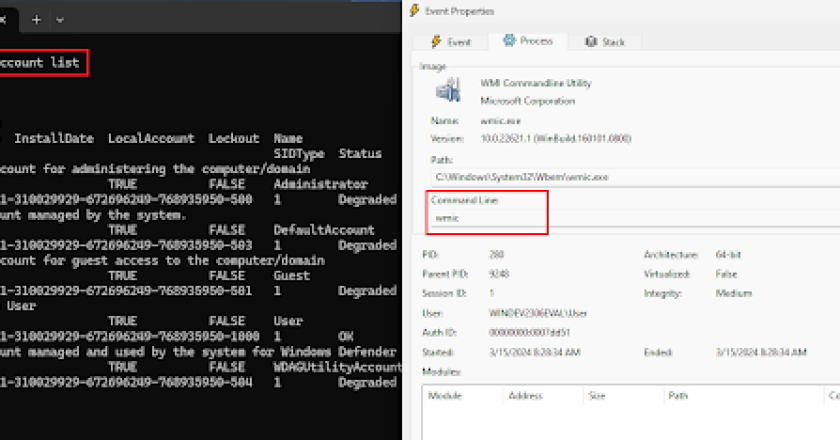

NoArgs is a tool designed to dynamically spoof and conceal process arguments while staying undetected. It achieves this by hooking …
WinDiff is an open-source web-based tool that allows browsing and comparing symbol, type and syscall information of Microsoft Windows binaries …
Handle hijacking is a technique used in Windows operating systems to gain access to resources and resources of a system …
C2-Hunter is a program designed for malware analysts to extract Command and Control (C2) traffic from malwares in real-time. The …
MSI Dump – a tool that analyzes malicious MSI installation packages, extracts files, streams, binary data and incorporates YARA scanner. …
A project created with an aim to emulate and test exfiltration of data over different network protocols. The emulation is …
A Nim implementation of reflective PE-Loading from memory. The base for this code was taken from RunPE-In-Memory – which I …
Hunt & Hackett presents a set of tools and technical write-ups describing attacking techniques that rely on concealing code execution …
In preparation for a VBS AV Evasion Stream/Video I was doing some research for Office Macro code execution methods and …
Koh is a C# and Beacon Object File (BOF) toolset that allows for the capture of user credential material via …